网络安全与网络安全与信息安全
计算机网络的安全是一项至关重要的任务。这是一个确保机密性和完整性的过程。如果一个系统的资源在所有情况下都按预期使用和访问,则系统被认为是安全的,但没有一个系统可以保证绝对安全,免受各种恶意威胁和未经授权的访问。
在本文中,我们将看到网络安全与网络安全与信息安全之间的区别。
网络安全:
网络安全是保护系统、网络和程序免受数字攻击的方法。网络安全涉及帮助和保护各种数字组件网络、数据和计算机系统免受未经授权的数字访问的技术。根据您连接的网络类型和您容易遭受的网络攻击类型,有多种方法可以实现网络安全。常见的网络安全风险:
- 社会工程学
- 蛮力
- 诱饵
- 勒索软件
网络安全:
网络安全是保护您的网络和数据的可用性和完整性的方法。它包括硬件和软件术语。有效的网络安全管理对网络的访问。它针对各种威胁并阻止它们进入或在您的网络上传播。常见的网络安全风险:
- 病毒、蠕虫和木马
- 拒绝服务 (DOS) 攻击
- 零日攻击
信息安全:
信息安全是为保护记录免遭未经授权的进入和使用而采取的措施。它提供机密性、完整性和可用性。信息安全是包含网络安全和网络安全的超集。对于任何大规模运作的企业或公司来说,这都是至关重要的。数据可以是电子的或物理的。常见信息安全风险:
- 使用权
- 破坏
- 可用性
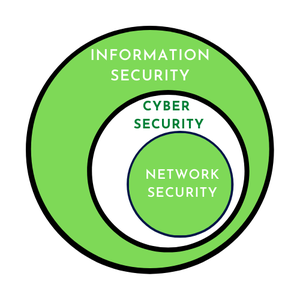
网络安全、网络安全和信息安全之间的区别:
| S.No. | Cyber Security | Network Security | Information Security |
|---|---|---|---|
| 01. | Cybersecurity is the method of protecting systems, networks, and programs from digital attacks. | Network Security is the method of protecting the usability and integrity of your network and data. | Information security is the measures taken to protect the records from unauthorized entry and use. |
| 02. | Cyber Security is a subpart of Information Security. | Network Security is a subpart of Cyber Security. | Cyber Security & Network Security comes under Information Security. |
| 03. | It protects anything in the cyber area. | It protects anything in the network area. | Information security is for information irrespective of the space. |
| 04. | It deals with protection from cyber attacks. | It deals with protection from DOS (Denial of Service) attacks. | It deals with the security of data from any kind of threat. |
| 05. | Cyber security attacks against cybercrime and cyber fraud. | Network Security attacks against trojans. | Information Security attacks against unauthorized access, disclosure modification, and disruption. |
| 06. | Cyber security ensures the security of the entire digital data. | Network security only ensures the security of transit data. | Information security ensures the protection of transit and digital data. |
| 07. | It deals with the security of the data resting. | It secures data traveling across the network by terminals. | It gives integrity, confidentiality, and availability. |
| 08. | Common Cyber Security Risks:
| Common Network Security Risks:
| Common Information Security Risks:
|