1. 代币化:
顾名思义,令牌化基本上是一种替换技术,它用称为令牌的随机生成的代码替换敏感数据。在这里,令牌通常用作原始数据的引用或占位符。它只是保留了数据的感觉和格式,也保护了数据主体的隐私。它通常用于信用卡处理以增加安全性。
例子 :
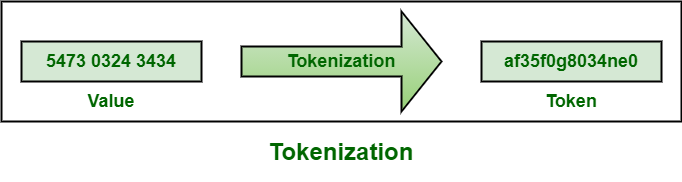
2. 加密:
加密,顾名思义,是将数学算法和其他一些秘密信息结合起来,以一种在没有适当密钥的情况下基本上不可能逆转的方式来转换或转换数据的过程。它只是使用算法将纯文本信息从已知的密文转换为不可读的信息。它也可以反转,以便授权人员可以查看和使用原始和敏感数据。它被认为是实现数据安全的最有效方法。
例子 :
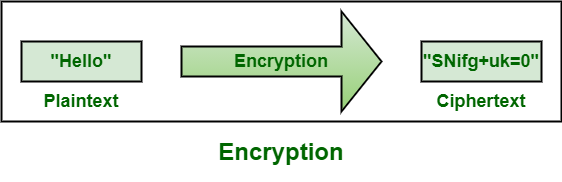
标记化和加密之间的区别:
|
Tokenization |
Encryption |
|---|---|
| It is a process of turning sensitive data into non-sensitive data usually known as tokens. | It is a process of encoding message, data, or file so that it can be accessed and read only by certain people. |
| It is important because it helps to reduce risk from data breaches and build trust with customers. | It is important because it helps to protect private information or sensitive data, and enhance security of communication among servers and client apps. |
| Its main objective is to swap out or substitute sensitive data such as payment card or bank account numbers with randomized number in same format but without any intrinsic value of its own. | Its main objective is confidentiality such as concealing content of message by translating it into code. |
| It can be offered only via web services. | It can be offered both locally and as web service. |
| It is best suited for structured data fields and is therefore mostly used to protect sensitive data in payment processing systems like credit card information or social security numbers. | It is best suited for unstructured fields or databases that are not stored in multiple system and for protecting files such as entire files or emails, and also supports structured data such as payment card numbers. |
| It is difficult to exchange data because of access to token database. | It is easier to exchange data because on can access original data if needed with decryption key. |
| It uses tokens to protect or secure data. | It uses secret keys to protect or secure data. |
| In this, if somehow token is intercepted, then it cannot be used to guess real values. | In this, if somehow key is intercepted, then too it can be used to decrypt all data it was used to secure. |
| It is an irreversible process. | It is a reversible process. |
| It generates token value randomly for plaintext and stores mapping in database. | It scrambles data so that only authorized parties can have access to data. |